
Identification and access management solution
Do you need a safe and modern management solution to handle users? Do you have a large number of apps and services? You know that they need to be secured and their user credentials need to be checked, with specific permissions (admin, guest, sales, etc). On the other hand, app users need a simple and unique way to login, also called the SSO (Single Sign On).
For safety and design, it’s not recommended to use Active Directory (AD) setup for workstations. A better practice is to use new realms, that are cloud-ready and lightweight.
The features that we require:
- Easy and fast setup
- Secure and standard
- Ability to create users, roles and groups
- Create app permission levels
- Generate JWT Tokens
- SSO
- Open Source
For all of this management solution, our recommendation is KeyCloak, a JBoss community project powered by Red Hat. It’s currently the main IAM software at RedHat.
Home page
Login page
Admin interface
Deploy using Docker + Traefik
Deploying is really easy. Basically, we need 2 pods, one for the KeyCloak instance and one more for the database (optional). You can choose the type you want (mysql, postgres, H2, etc).
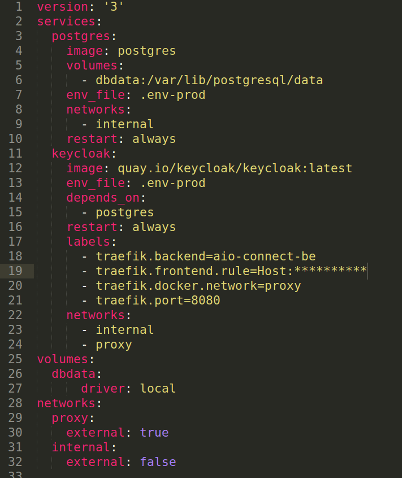
.emv file
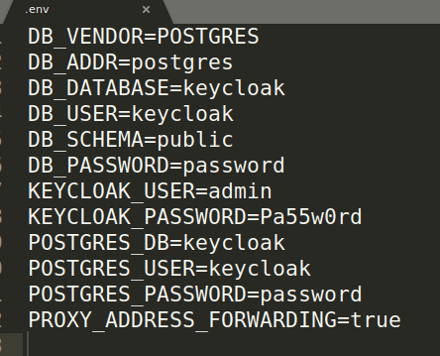
The PROXY_ADDRESS allows us to communicate through HTTP to KeyCloak, but also to forward a flag to indicate if the source query was HTTPS or not.

Create your DNS, make it match your Traefik label, then build & run the compose-file.
Create Realms, clients and users
Now, login to your newly installed KeyCloak on your browser. On the administration page, fill in the fields with your credentials. You may need to check the .env file.
Creating new realms
Realms handle users, groups, roles and clients. Each of them is isolated between realms.
Next, you will need one client ID for the application and one initial user.
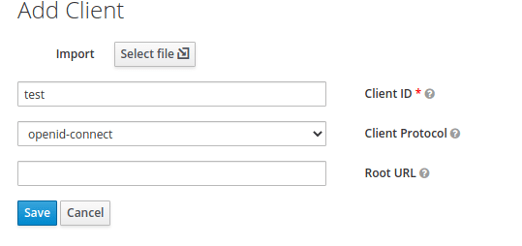
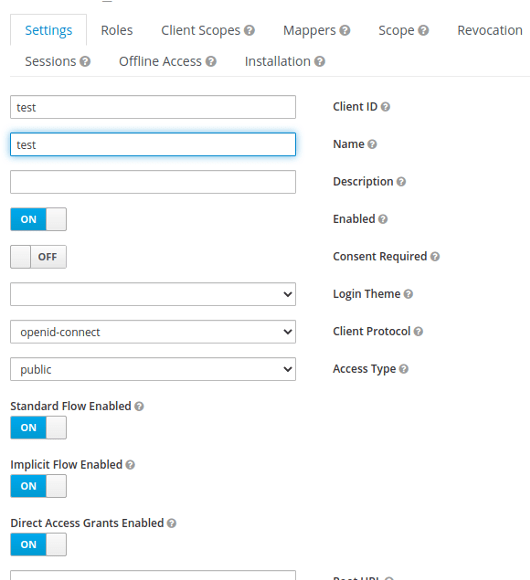
The most important step is to validate the redirect URL. For this, you’ll need to set up the app where user will use the token. Use regex if you want to cover more URLs.
Example: https://locallhost.com/
Creating users
Select create User, fill out all fields, press save, then click on the Credential tab to set up a temporary password.
Now, you can use KeyCloak lib on your front and / or backend, or handle the token yourself and forward it between each query. To do this, here is a simple workflow:
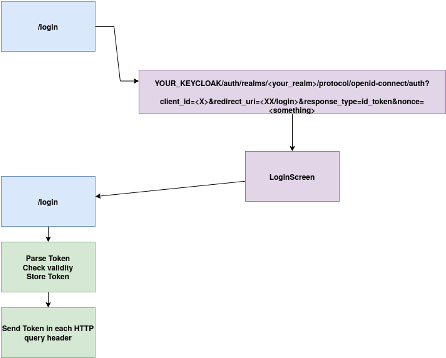
Some useful links:
- Certificate and algo used : https://DOMAIN.COM/auth/realms/REALM/protocol/openid-connect/certs
- Public_key https://DOMAIN.COM/auth/realms/REALM/


